There’s a maxim in IT security that you can’t protect your assets if you don’t know where they are. Simple. Clear. But for the CISO, the kind of headache that keeps them up at night.
Understanding where your assets are — whether they are local or in your datacenter, remote at a hosting site or disaster recovery center, or stored in the cloud — can serve the needs of multiple corporate masters.
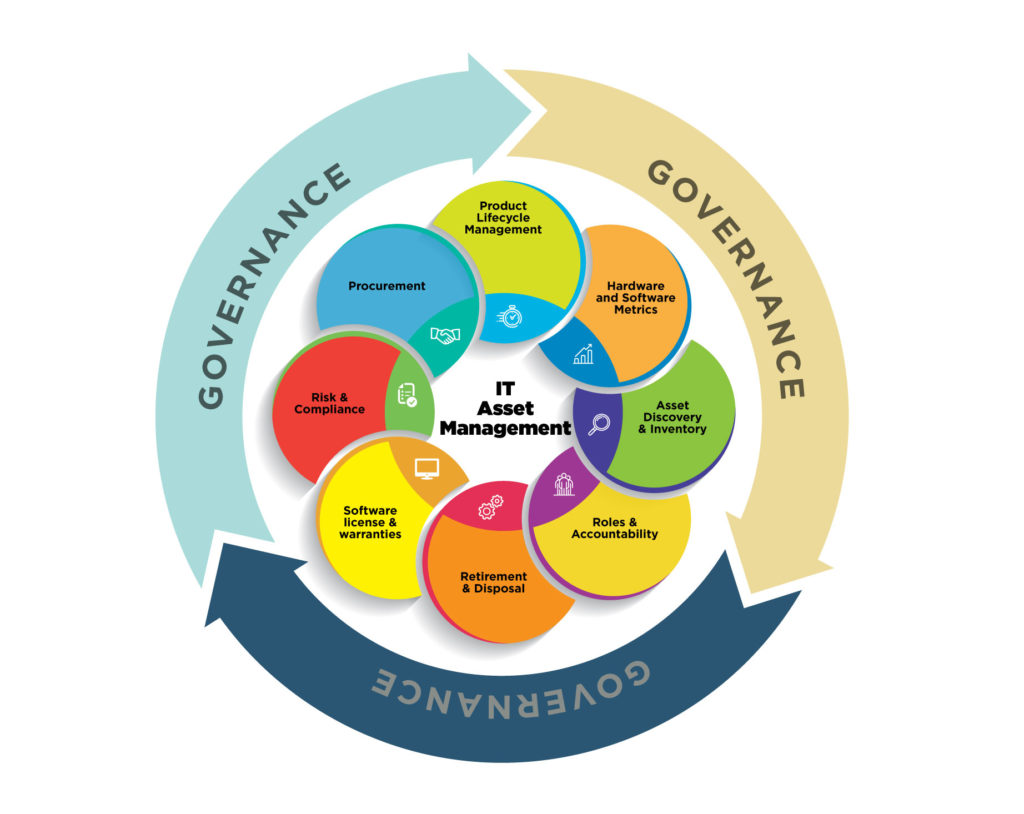
For the CISO, knowing where data and computing resources are helps create a framework for a data and cybersecurity plan. To the chief governance, risk and compliance officer, it helps identify potential areas of risk and lays the groundwork for building a compliance plan that can stand the scrutiny of auditors enforcing the plethora of compliance rules and regulations. The corporate counsel will need such a framework to defend against potential consumer, corporate and shareholder lawsuits should there be a breach. The board and senior management also need this data to ensure they are meeting their fiduciary responsibilities to shareholders as well as their own legal obligations to the company. This is hardly a comprehensive list but rather underscores why developing an asset and lifecycle management program is essential for good corporate governance.
Here are just a few ways asset management works for your CISO, the cybersecurity team and other key stakeholders:
- Asset management serves a variety of functions. They include aiding the finance and procurement departments in understanding the value of existing assets and where they are located. This is essential when developing budgets and determining when to upgrade an asset as opposed to simply replacing it.
- Asset discovery and inventory helps the security team identify potentially rogue devices and shadow IT inappropriately connected to the network. It also can aid in identifying unused for legacy hardware that is still connected to the network but might not have modern security resources installed.
- From a cybersecurity perspective, knowing what assets you have and where they are is an essential part of incident response and forensics investigations.
- Understanding software licenses and warranties can help you avoid the financial vulnerability posed by those that are out of date or expired.
- Knowing what assets you have and where they are helps the governance, risk and compliance teams meet their corporate and legal responsibilities.
