
As companies meet increasingly stringent compliance regulations, the stresses on IT asset management also escalates. This raises two important questions: Can a company fully document its workflow from one asset to another? Can a company be sure that that personally identifiable information (PII), personal health information (PHI) and other protected data is not moving through unaccounted-for assets, either in the cloud or on premises?
Workflow is critical, yet how many companies actually understand how their workflows are organized? As it turns out, the answer to this question is too few.
Industry experts stress the importance of consistent baseline protocols and compliance documentation standards. This can be particularly challenging for widely distributed and geographically dispersed businesses — do they know what their processes are? If the answer to that is no, they had better find out now, the experts agree.
Kevin L. Jackson, CEO and COO of the Manassas, Va-based consulting company GC Globalnet, brings these issues and challenges into stark relief. Jackson says that “workflows are normally documented as interactions between company organizational components,” whereas “IT assets are typically tracked with procurement workflows … acquired, managed and disposed of like any other physical assets.”
But there is a problem with this approach. “IT devices are used to manipulate and manage an even more important asset — namely, data. [But] data itself is not normally managed as an important asset [so that] data workflows are also not independently managed,” he says.
The first step to gaining control, says Jackson, is to classify data. This means recognizing what kind of data is involved, identifying the types of information it contains, and how it does or does not map into compliance regimes related to PII, PHI, financial data, and the like.
To that end, he recommends regular inventories — which could occur as part of scheduled audits, compliance checks, or independently — carefully checked against data privacy, protection, and other applicable compliance or regulatory requirements.
Digging into baseline protocols
Jackson’s primary focus is on maintaining security and protection when cloud computing plays into a company’s IT infrastructure. He works with his clients to acquaint them with the Security Guidance v4.0 guidelines from the Cloud Security Alliance (CSA). He also makes regular and strenuous use of that organization’s Cloud Controls Matrix (CCM).
The CSA describes the CCM as “a cybersecurity control framework for cloud computing, composed of 133 control objectives … structured in 16 domains that cover all key aspects of … cloud technology.” Between this standard guidance and the control objectives, he finds that most businesses can address data classification and managing their data flows by implementing their best practices and recommendations.
Jackson’s formulation for obtaining buy-in and active support for proper compliance and data protection is straightforward. He asserts that this requires “strict enforcement of formal organizational data security and privacy policies coupled with required training and education.”
It is one thing for small or midsize companies to have challenges with managing compliance, but even the largest firms have yet to find a way to overcome these overwhelming issues. A 30-year cybersecurity veteran and senior IT security executive at the U.S. subsidiary of a Fortune 10 petroleum company who asked not to be identified due to corporate policies on speaking to the media (for the sake of this story we will call the executive OilMan) put things succinctly: “You have to play ‘Bad Cop’ with upper management.
“The CEO and the CFO are usually legally responsible for verifying that the company is in compliance, so you have to acquaint them with the risks involved should they be charged with significant compliance deficiencies or failures,” he notes. “These can involve jail sentences of 10-25 years, and multimillion-dollar fines. This usually gets their attention.”
OilMan goes on to observe that “upper management must believe and invest in the compliance process for such efforts to succeed and deliver responsible risk management. Once upper management, and the risk, financial and security teams understand the risks they face, they can decide which ones they must tackle, and which once they can accept.”
But this is not a set-it-and-forget-it operation, either. OilMan recommends that companies create a risk registry that identifies data- and workflows and their associated risks, and that they make its review and management part of the ongoing, periodic compliance review and audit lifecycle.
“Too often,” says OilMan, “operations people tasked with keeping IT running and all systems working, also find themselves responsible for data security, integrity, protection, and privacy matters. This seldom ends well, in my experience.”
He says, “Compliance management needs its own mandate, its own people and resources, and a clear sense of mission and responsibilities. The only way a CEO or CFO can sign off on compliance is to hire people who’ve been properly trained, have the right skills and knowledge, and know how to ensure that the company can survive a hostile audit with no more than minor deficiencies.”
To that end, OilMan is keen on several technical certifications, including the ISACA Certified Information Systems Auditor (CISA), Certified in Risk and Information Systems Control (CRISC) and Certified in the Governance of Enterprise IT (CGEIT). Other certifications OilMan recommends are the International Information Systems Security Certification Consortium’s — commonly known as (ISC)2 — Certified Information Systems Security Professional (CISSP) certification and the International Association of Privacy Professional’s (IAPP) Certified Information Privacy Professional (CIPP) accreditation. CIPP comes in U.S. and European versions to differentiate between the compliance regimes that include Sarbanes-Oxley Act (SOX), Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standards (PCI DSS) in the U.S. and the European Union’s General Data Protection Regulation (GDPR) and other initiatives.
Proper risk management is key
OilMan knows from more than a decade’s worth of experience in working compliance policies, regimes, reviews and audits that “everything starts from an understanding of risk. You must spell out the company’s ‘risk appetite’ in great detail.” Then, says OilMan, the risks the business decides to manage must have controls associated with them.
By implementing such controls, and monitoring how they are used or abused, the risk management team can fully understand what is happening with and to the data in the business’s workflows and proactively work to avoid or mitigate risk.
Some return to the “Bad Cop” role might be required, he says. “I’ve learned to pose questions like ‘Do you want us to be in the news?’ or ‘How will this affect our reputation?’ and ‘Do you know how much this could cost if unchecked?’” OilMan observes that “it’s easy to get management support, and marching orders to match, when the risks are up close and personal for those people.”
Bill Alderson, CEO of the Austin, Texas-based networking security and data protection consulting company HOPZERO, has focused on wire- and application-level network security for more than three decades. He tells this story about a major client:
“One of my Fortune 100 energy clients splits up their devices and addresses disposition, updates and asset management. The network manager has a small group that manages about 4,000 network components. They continuously surplus, modernize or update these products. They use as many automation tools as possible, but it ultimately entails a significant manual step by step processes and effort,” he says.
“They are tasked with touching each piece of equipment at least once a year,” he continues. “On occasion, a particularly egregious security patch will cause them to prioritize. These systems are subject to compliance audit and their daily security information flow updates and reports on current levels and events.”
Alderson even has a map to show where these managed devices reside on the globe (all the major continents included).
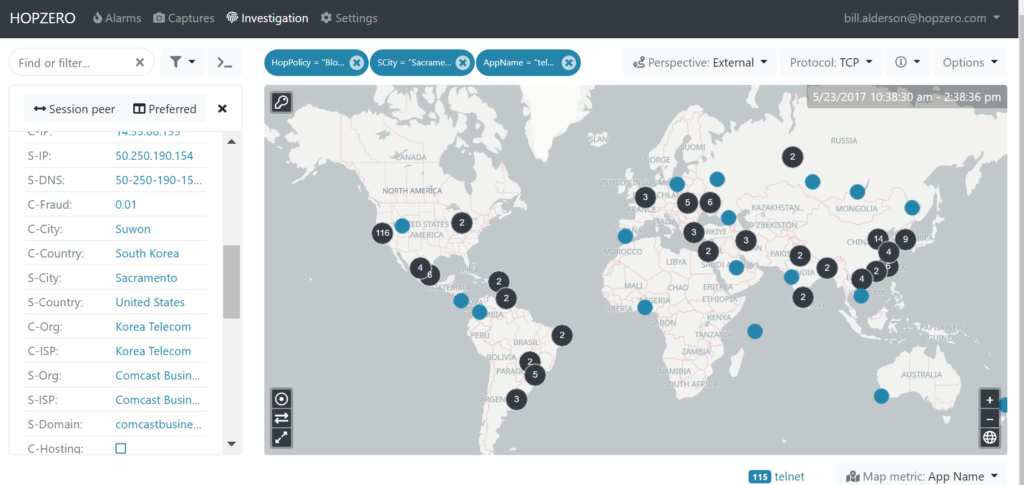
Alderson says, “It’s essential to know — and monitor — where and how data flows into and out of the business, on premises, in branch or remote offices, and all the clouds (private, public and hybrid) in use. We’ve got it documented and visualized.”
He also worked on creating what he calls “one-click compliance reports” for his clients. These, he says, “show where vital server data is exfiltrating, leaking out the firewall. Another click and I export the list of devices to an Excel spreadsheet for formal reporting.”
These then become the focus of mitigation and expungement efforts, working with search engine providers to remove sensitive data from public view. His approach is to advise clients to recognize that “every security standard requires 24/7 recording of every communication session going into a data center. We record every … session adding security and performance metrics.” This pays added benefits to companies, he asserts, because “discovery and visualization of where data is traveling creates a regular desire to see what changes.”
Alderson also advises that companies pay close attention to their logs, where they can find treasure troves of information about data accesses and changes, data motion, and data protection. “Log analysis tools provide excellent visibility,” he says, “and help companies keep track of what’s being accessed, who’s accessing it, and much more.”
Achieving compliance is a journey, not a destination, the experts agreed. They all clearly believe that compliance requires an ongoing process, with clear-cut policies and controls to match. Little wonder that compliance and data protection must be part of the IT lifecycle for today and for as long as data and workflows provide key to business activity and success.
